SAE 3CYBER03 DESIGNING A SECURE MULTI-SITE NETWORK
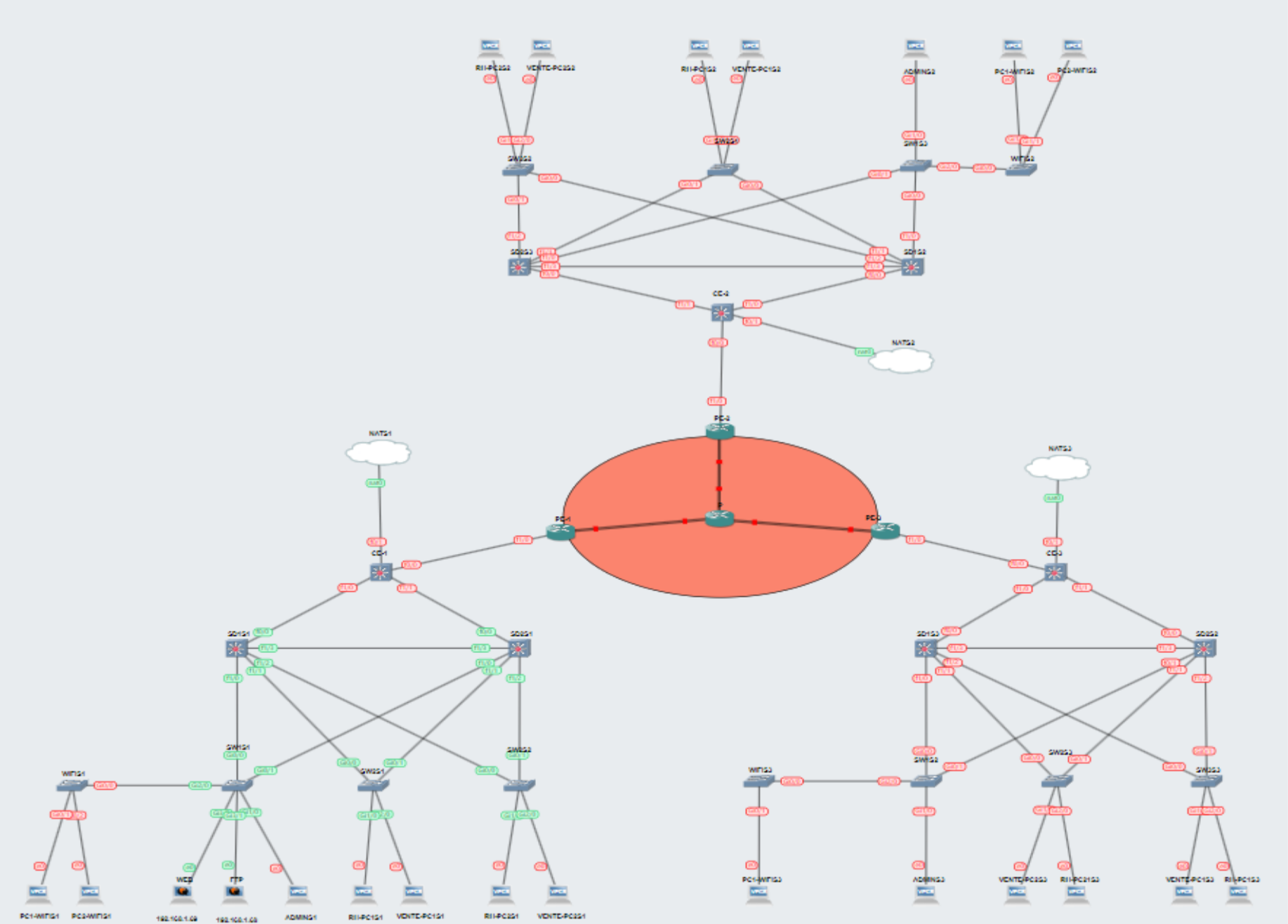
As part of my studies in Networks and Telecommunications, I had the opportunity to participate in the SAE 3.CYBER.03 project. The primary objective of this project was to design a secure and reliable network infrastructure for a company with three distant sites. This endeavor allowed me to apply my theoretical knowledge and develop essential technical skills in cybersecurity and network management.
Project Overview
The company involved in this project operates across three geographically dispersed sites, requiring seamless and secure connectivity to enhance communication and collaboration among teams. To address this need, we implemented an MPLS VPN (Multiprotocol Label Switching Virtual Private Network) solution, creating a robust interconnected network. This approach not only ensured efficient communication between different sites but also reinforced the security of data exchanges.
Network Architecture
Three-Tier Hierarchical Model
The network infrastructure was designed using a three-tier hierarchical model comprising the Access Layer, Distribution Layer, and Core Layer. Each layer plays a crucial role in building a resilient and high-performing network.
Access Layer
The Access Layer serves as the first point of connection for end-users and devices. It provides direct connectivity for devices such as workstations and servers. In our project, each site (Site1, Site2, and Site3) connects to the MPLS Backbone using access switches. VLAN segmentation at this layer optimizes traffic management by logically isolating different groups of devices, facilitating communication control, and enhancing security.
Distribution Layer
The Distribution Layer aggregates traffic from the Access Layer switches, manages inter-VLAN routing, and connects to the MPLS Backbone. It also handles local services such as DHCP for dynamic IP address allocation and HSRP (Hot Standby Router Protocol) for router redundancy. Access Control Lists (ACLs) are implemented at this layer to define security policies, controlling which traffic is permitted or denied. The interconnection of access switches allows seamless data exchange between VLANs, while inter-VLAN routing enables communication across different VLAN segments.
Core Layer
The Core Layer is the central hub responsible for the overall management and routing of network traffic. It handles global routing between different sites, aggregates traffic from the Distribution Layer, and ensures optimal use of MPLS links through high-availability mechanisms like redundancy and load balancing. Dynamic routing protocols such as OSPF (Open Shortest Path First) are employed to automatically adjust routing paths based on network topology, ensuring maximum performance and resilience.
VPN MPLS Configuration
Creating VRFs (Virtual Routing and Forwarding)
The first step in configuring the MPLS VPN was setting up VRFs on the Provider Edge (PE) routers (PE1, PE2, and PE3). VRFs allow us to segment client traffic, isolating routes and traffic for each client independently. For this project, a single VRF named "client" was created, with the flexibility to add more VRFs for additional clients in the future.
Assigning VRFs to CE Interfaces
VRFs were associated with interfaces directly connected to Customer Edge (CE) routers (CE1, CE2, and CE3) to isolate traffic and manage routing independently. Additionally, the OSPF routing protocol was configured on these interfaces to facilitate efficient communication with the CE routers.
OSPF and BGP Configuration
OSPF was implemented between the Provider Edge (PE) and Provider (P) routers to dynamically exchange routing information. BGP (Border Gateway Protocol) was also configured between PE routers using their loopback interfaces, enabling robust and flexible traffic management across the network.
Route Distinguishers and MPLS
Route Distinguishers (RDs) were added to differentiate networks of different clients, allowing for packet routing even when multiple clients use identical IP prefixes. MPLS was activated on PE routers and the P router, enabling label-based packet switching and ensuring rapid and efficient data transmission across the interconnected network.
LAN Configuration
VLAN Configuration
Each L3 switch at Sites 1, 2, and 3 was configured with designated VLANs, assigning specific ports to each VLAN. For instance, on Switch1 at Site 1, ports Gi1/0-3 were assigned to VLAN 99 (Network Administration), Gi2/0-3 to VLAN 40 (Wifi), and Gi3/0-3 to VLAN 50 (Servers). This setup ensures clear and effective network segmentation, enhancing both management and security.
Trunk Configuration
Trunks were configured on ports interconnecting the switches, allowing authorized VLANs to pass between switches. This ensures smooth and secure communication across VLAN segments at different sites.
DHCP and NAT Configuration
At Site 1, the DHCP server (SD1S1) was configured to dynamically assign IP addresses to VLANs 10, 20, 40, 50, and 99, while excluding addresses reserved for HSRP and fixed devices. NAT (Network Address Translation) was set up on CE routers to enable the translation of LAN IP addresses to public addresses, facilitating secure internet access for end-users.
Server Installation and Configuration
Web Server
An Apache2 web server was installed and configured to provide secure web services via HTTPS. SSL/TLS certificates were generated using OpenSSL to encrypt communications between clients and the server, enhancing data security.
FTP Server
A secure FTP server was set up using VSFTPD, allowing only authenticated users to access files. Additional security measures, such as enabling passive mode and chrooting users, were implemented to protect the server from unauthorized access and potential attacks.
Access Control Lists (ACLs)
ACLs were implemented on all L3 switches across the three sites to precisely control network traffic. These ACLs allow, for example, the Admin VLAN to communicate with other VLANs while restricting unauthorized access. This configuration strengthens overall network security by enforcing strict access and traffic rules.
SSH Configuration on L2 Switches
To enable secure remote management of L2 switches, SSH was configured. An IP address was assigned to VLAN 99, a domain name was set, and RSA keys were generated to secure SSH connections. VTY lines were configured to accept only SSH connections with secure passwords, ensuring that only authorized personnel can access switch configurations.
Connectivity Testing
Inter-VLAN Routing
Connectivity tests were performed between different VLANs at each site to ensure proper inter-VLAN routing. VLANs for HR, Sales, Wifi, and Admin were interconnected, enabling secure and efficient communication across various services within the company.
Inter-Site Connectivity
Ping tests from CE routers to VLAN interfaces of other sites confirmed robust and secure connectivity between sites via the MPLS VPN. This interconnection ensures that data can flow securely and efficiently between different company locations.
WAN Connectivity
Additional tests involved pinging external domain names like "google.com" from workstations at each site. These tests verified both DNS resolution and general internet connectivity, confirming that NAT and routing configurations were functioning correctly.
MPLS VPN Testing
Packet captures using Wireshark during inter-site connectivity tests confirmed the proper functioning of the MPLS VPN, evidenced by MPLS encapsulation within IP packets. This analysis validated the security and efficiency of the network traffic across the interconnected network.
Conclusion
The SAÉ 3.CYBER.03 - Designing a Secure Multi-Site Computer Network project successfully implemented a complex and secure network infrastructure that meets the connectivity and security needs of modern businesses. By employing a three-tier hierarchical architecture—Access, Distribution, and Core Layers—we structured network traffic effectively, ensuring reliable connectivity between the company's different sites.
VLAN segmentation and detailed IP addressing optimized traffic management and enhanced network security by isolating services and users based on their specific needs. The implementation of an MPLS VPN, along with meticulous configurations of VRFs, OSPF, and BGP, significantly improved network security and efficiency, allowing flexible and secure traffic management between clients and sites.
Setting up LAN services, including DHCP, HSRP, and NAT, as well as installing and configuring Web and FTP servers, ensured continuous and high-performing network services. ACLs, applied thoughtfully, reinforced network security by strictly controlling access and network traffic.
Remote administration of L2 switches via SSH added an extra layer of flexibility and security, enabling the network administration team to manage switches quickly and securely. Comprehensive connectivity tests, both at the inter-VLAN and inter-site levels, demonstrated the effectiveness and reliability of our network infrastructure. Packet analyses with Wireshark confirmed the proper operation of the MPLS VPN and the secure handling of network traffic.
In summary, this project not only achieved its initial goals of providing secure and efficient connectivity between the company's different sites but also laid the foundation for an adaptable and scalable network infrastructure. This infrastructure is well-equipped to meet future requirements and technological advancements in the fields of cybersecurity and computer networking.
This project has significantly enhanced my technical skills in cybersecurity and network administration, as well as my ability to manage complex projects, solve real-world problems, and collaborate effectively within a team. It stands as a valuable addition to my portfolio, demonstrating my capability to design and deploy sophisticated and secure network solutions in a professional setting.
